Automating Two-Factor Authentication (2FA)
Some applications enforce Two-Factor Authentication (2FA) using OTPs generated by authenticator apps such as Google Authenticator, Microsoft Authenticator, or Authy.
DevAssure supports testing these flows through the Authenticator.Get Authenticator OTP test action.
This action generates the OTP (One-Time Password) which can be used in test autoamtion. To do this, DevAssure requires the shared secret that is provided when the authenticator is first configured.
This section explains how to extract the secret from the QR code and use it in your test automation.
Getting the Secret from the QR Code
When setting up an authenticator app, applications typically show a QR code.
This QR encodes a URI in the following format :
otpauth://totp/<LABEL>?secret=<SECRET>&issuer=<ISSUER>
Example QR URI
otpauth://totp/example.com:[email protected]?secret=JBSWY3DPEHPK3PXP&issuer=ExampleApp
- secret →
JBSWY3DPEHPK3PXP(Base32 encoded shared key) - issuer → The application or service name (e.g.,
ExampleApp) - label → Usually email or username
Steps to Extract the Secret
- Scan the QR code with a QR decoder tool (instead of the authenticator app).
- You can use online tools, or libraries such as
zxing(Java),qrcode(Python), or browser extensions.
- You can use online tools, or libraries such as
- Extract the URI (starts with
otpauth://). - Parse the query string → copy the value of secret.
- Store the secret securely in the encrypted DevAssure Secret.
- DevAssure generates an OTP using this given secret.
- Complete the Authenticator App setup
Using Authenticator.Get authenticator OTP
Inputs
- Secret: The secret extracted from the QR code.
Outputs
- OTP: A 6-digit (or 8-digit) numeric code valid for the current time window (usually 30s).
Example: Using Authenticator.Get authenticator OTP in a Test Flow
The following example demonstrates how to use the Authenticator.Get authenticator OTP action in a DevAssure automation sequence.
Test Flow
This flow replicates a real-world login with 2FA. Instead of reading the OTP manually from an authenticator app, DevAssure generates it automatically using the stored secret. The OTP is dynamically valid for the current 30-second time window, ensuring tests run without manual intervention.
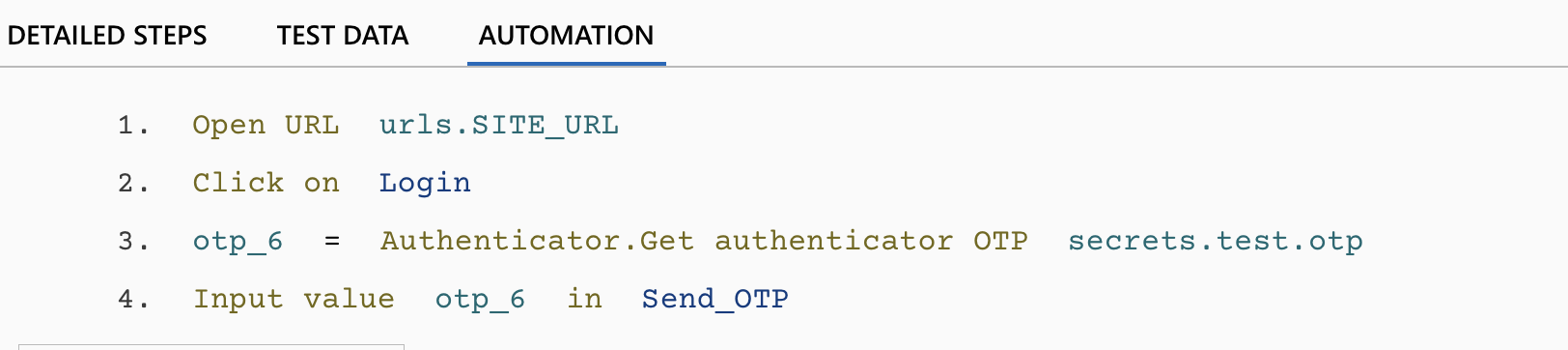
Open URL
Open URL urls.SITE_URL
- Navigates to the target application under test.
- The URL is parameterized via urls.SITE_URL for environment flexibility.
Click on Login
- Click on Login
- Simulates a user clicking on the login button to initiate authentication.
Generate OTP from Secret
otp_6 = Authenticator.Get authenticator OTP secrets.test.otp
- Uses the Authenticator.Get authenticator OTP action to generate a time-based OTP. secrets.test.otp is the stored secret key (fetched earlier from the authenticator QR code). The generated OTP is stored in the variable otp_6.
Enter OTP into Form
Input value otp_6 in Send_OTP
- Types the generated OTP (otp_6) into the OTP input field (Send_OTP).
Handling Existing Authenticator Installations
If a user has already installed and configured an authenticator app before setting up automation, the secret is not directly accessible.
Solution: The user can uninstall and re-install the authenticator app, then re-scan the QR code in DevAssure to fetch the secret.
This ensures that the automation framework has the same OTP source as the authenticator app.
With this setup, DevAssure can automatically handle OTP-based 2FA during test execution.
You must already have the ssecret from when the authenticator was first set up. Without it, OTP generation isn’t possible.
If your system under test uses SMS/email OTPs, then this action won’t apply—it’s only for app-based authenticators (TOTP).